Digital Transition Risk: Why Non-Tech Boards Inherit Tech-Grade Exposure
Digital modernisation is often treated as an operational upgrade. In reality, it transforms how organisational risk behaves. This paper examines why boards of traditionally structured organisations now inherit technology-grade exposure across cybersecurity, data, vendors, and AI.

Institute for Systems Integrity (ISI)
Co authors:
Kishore Madhusudanan, B.Tech, CISM, EMBA (Melbourne Business School)
Security Architect | Zero Trust & Cloud Security Resilience Architecture | Executive MBA | Certified Information Security Manager
Dr Alwin Tan, MBBS, FRACS, EMBA (Melbourne Business School)
Senior Surgeon | Governance Leader | HealthTech Co-founder
Harvard Medical School — AI in Healthcare
Australian Institute of Company Directors — GAICD candidate
University of Oxford — Sustainable Enterprise
(Disclaimer: The views and opinions expressed in this post are strictly those of the authors in their personal capacity. They do not necessarily reflect the official policy or position of any current or former employer, organization, or affiliate.)
Executive Summary
Digital modernisation is often described as an operational upgrade — a move toward efficiency, convenience, or innovation.
From a governance perspective, it represents something far more consequential:
a structural transformation of enterprise risk behaviour.
Industry classification (“non-tech”) no longer predicts organisational exposure to:
– Cybersecurity incidents
– Data compromise
– Systemic operational disruption
– Artificial intelligence (AI) risk
As organisations become dependent on cloud-based systems, electronic records, digital imaging, online billing, telehealth platforms, vendor-managed infrastructure, and AI-enabled tools, boards inherit technology-grade risk dynamics, regardless of sector identity.
This transition demands recalibration of board oversight, accountability structures, and resilience capability.
1️⃣ Digital Adoption Is Also Risk Adoption
Modern organisations increasingly rely on:
✔ Cloud-based systems
✔ Electronic records and workflows
✔ Digital imaging and diagnostics
✔ Online billing and payment platforms
✔ Telehealth and remote services
✔ Vendor-managed infrastructure
✔ AI-enabled tools
These shifts rarely occur through a single transformative decision. More commonly, they emerge through a series of incremental, rational improvements.
Each step appears modest.
Collectively, they reshape:
– Threat exposure
– Failure speed
– Interdependency behaviour
– Detection challenges
– Recovery complexity
Digital dependency changes how disruption originates and how harm propagates across the system.
From a systems integrity perspective, digitalisation often introduces:
⚠ Fragility concentration
⚠ Dependency amplification
⚠ Latent failure conditions
2️⃣ The Persistence of the “Non-Tech” Mental Model
Despite this shift, many boards continue to anchor governance assumptions to legacy identity:
❌ “We are not a technology company.”
❌ “Technology supports rather than defines operations.”
Yet digital infrastructure now underpins continuity, service delivery, and stakeholder trust across nearly all sectors.
Operational resilience increasingly depends on:
✔ System availability
✔ Data integrity
✔ Cyber resilience
ISI’s principle of Integrity as a System Property emphasises that vulnerability emerges not from isolated components but from:
✔ Interactions
✔ Dependencies
✔ Decision pathways
✔ Feedback loops
Digitalisation fundamentally reshapes these dynamics, irrespective of industry classification.
3️⃣ Digital Fragility Behaves Differently
Traditional operational risk models often assume:
– Gradual degradation
– Observable warning signals
– Localised disruption
– Linear recovery
Digital failure modes exhibit markedly different characteristics:
✔ Rapid cascade potential
✔ Latent compromise
✔ Non-linear disruption
✔ Complex restoration pathways
Disruption affecting cloud platforms, electronic records, billing systems, or vendor-managed infrastructure may scale quickly and unpredictably.
What begins as a technical anomaly can become an enterprise-wide event.
4️⃣ Systems Drift: The Hidden Precursor
ISI’s Systems Drift Model offers a critical interpretive lens.
Under pressure, organisations may:
– Normalise temporary workarounds
– Tolerate minor control exceptions
– Defer resilience investments
These adaptations are rarely reckless. They are often pragmatic responses to competing demands.
Over time, however, they may shift the system from:
✔ Controlled → ⚠ Marginal → ❌ Unstable
Cybersecurity incidents and data breaches frequently represent late manifestations of accumulated drift, rather than sudden breakdowns.
5️⃣ Governance Implications for Boards
Cybersecurity oversight
Digital dependency elevates cybersecurity from a technical concern to an enterprise continuity issue.
Boards must oversee:
✔ Detection capability
✔ Control effectiveness
✔ Incident response readiness
✔ Recovery resilience
Frameworks such as NIST CSF 2.0 and AICD Cyber Security Governance Principles reinforce that cybersecurity sits firmly within board accountability.
Data governance
Digitisation concentrates high-consequence assets.
Failures frequently reveal:
⚠ Ownership ambiguity
⚠ Access control weaknesses
⚠ Boundary failures
Data breaches are therefore governance, trust, and regulatory events — not merely IT incidents.
Third-party and vendor dependency
Vendor-managed infrastructure alters:
✔ Control boundaries
✔ Visibility
✔ Recovery dependency
Boards must govern vendor ecosystems as risk-bearing system components.
Artificial intelligence (AI) risk
AI-enabled tools increasingly influence:
✔ Decisions
✔ Workflow automation
✔ Analytics and optimisation
✔ Stakeholder interaction
AI adoption introduces governance challenges involving reliability, bias, explainability, and accountability.
ISI’s Pause Principle highlights the need for structured reflection and oversight in high-speed, AI-influenced environments.
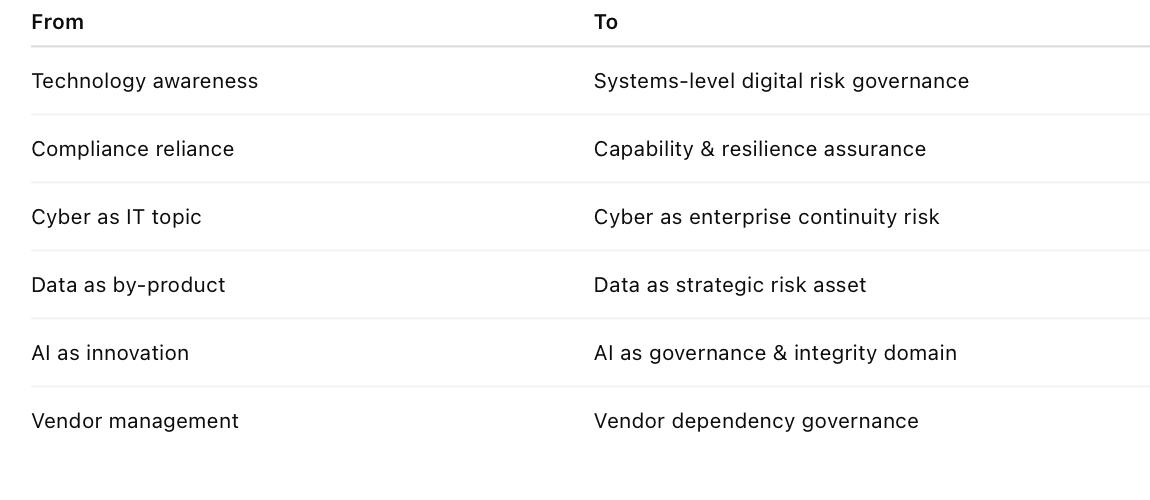
6️⃣ Recalibrating Board Oversight
Boards must transition governance posture:
7️⃣ Early Warning Signals
Boards should treat the following patterns as governance diagnostics:
⚠ Overconfidence in compliance assurance
⚠ Absence of detection or response metrics
⚠ Lack of recovery testing
⚠ Fragmented data accountability
⚠ AI adoption ahead of governance controls
⚠ Vendor dependency without failure scenarios
Such signals often indicate system drift rather than isolated control gaps.
Conclusion
Digital modernisation fundamentally transforms organisational risk behaviour.
Reliance on cloud-based systems, electronic records, digital imaging, online billing, telehealth platforms, vendor-managed infrastructure, and AI-enabled tools introduces technology-grade fragility across sectors traditionally regarded as non-technical.
Cyber incidents, data breaches, and AI-related failures frequently represent:
❌ Not sudden breakdowns
⚠ But accumulated integrity drift
Industry identity no longer mitigates digital exposure.
Systems integrity determines organisational resilience.
References
Australian Institute of Company Directors (AICD) 2024, Cyber Security Governance Principles (Second edition), AICD and Cyber Security Cooperative Research Centre, Sydney.
Australian Institute of Company Directors (AICD) 2025, Data Governance Foundations for Boards, AICD, Sydney.
Australian Cyber Security Centre (ACSC) 2023, Essential Eight Maturity Model (November 2023), Australian Government, Canberra.
International Organization for Standardization (ISO) 2022, ISO/IEC 27001:2022 Information Security Management Systems, ISO, Geneva.
Institute for Systems Integrity (ISI) n.d., Integrity as a System Property.
Institute for Systems Integrity (ISI) n.d., Systems Drift Model.
Institute for Systems Integrity (ISI) n.d., Stress–Signal Conversion Model.
Institute for Systems Integrity (ISI) n.d., Pause Principle.
National Institute of Standards and Technology (NIST) 2024, Cybersecurity Framework (CSF) Version 2.0, NIST, Gaithersburg.
National Institute of Standards and Technology (NIST) 2023, Artificial Intelligence Risk Management Framework (AI RMF 1.0).
Office of the Australian Information Commissioner (OAIC) n.d., Notifiable Data Breaches Scheme, OAIC, Sydney.
World Economic Forum (WEF) 2024, Global Cybersecurity Outlook 2024, World Economic Forum, Geneva




